Being a security expert is important for every hacker. It’s a good thing to be able to identify vulnerabilities in web applications. Still, it also helps you access private information and read sensitive data. In this article, we will show you how to hack your website with vulnerabilities as well as some examples of vulnerable websites from popular hacking websites like Hack My Website or Simple Hacking Guide (refer back to their home pages if you want more info).
Consequences of vulnerabilities in a web application
The consequences of web application vulnerabilities can be divided into three categories:
- Business impact and loss of revenue,
- User experience, and
- Security policy violations.
How to be a white hat hacker?
First and foremost, you have to be ethical. You should never steal anything. You should never destroy anything. You should never use your knowledge for malicious purposes.
Second: If a hacker is hacking into your website, they will look for known vulnerabilities they can exploit to gain access and take over the system or database behind it. Suppose there are no vulnerabilities at all because we did a good job protecting our servers against attacks. In that case, hackers try to access servers using brute force attack, which means trying all sorts of passwords until he gets lucky enough!
What are the programming languages used for web application hacking?
Web applications are written in different programming languages, such as PHP, Python, JavaScript, and Ruby, but not only. They can be developed using any of these languages or a combination of two or more.
PHP is a scripting language that was created by Rasmus Lerdorf in 1995. The name stands for “Personal Home Page.” It has been used to develop websites since 1998, when it was first released as an open-source project under a GPL license, allowing anyone to use it freely without paying royalties if they wish to do so.
Python is another popular choice for building web applications because its syntax resembles a natural language like English. Hence, developers find it easy to learn new concepts quickly without having any difficulty understanding them later on when working on other projects too…
Web Application Security Testing Methodology
Web application security testing methodology is a process of identifying and verifying potential vulnerabilities in web applications. It is an important step before launching a website or application. The process involves analyzing the application, identifying potential vulnerabilities, and determining how to fix them.
It’s not just about finding bugs in your code—you also need to look at the architecture level. How you built your site from scratch so that you can make sure everything is as secure as possible before releasing it publicly!
A few examples of vulnerabilities on webapplication/ web app, more can be found: The OWASP Top 10 Vulnerabilities of 2021
Cross-Site Scripting (XSS) vulnerabilities
Cross-site scripting (XSS) is a vulnerability that allows an attacker to inject malicious code into a website. For example, an exploit can be used to steal user data, access other pages on your site, change the content and layout of your page, or even add new functionality to it.
The consequences of XSS vulnerabilities can be severe: attackers can steal sensitive information such as usernames and passwords and use it for fraud. They also make users vulnerable to malware attacks because they can be exploited by hackers who may inject viruses into their browsers while visiting other websites.
Injection code example:
http://target.com/page?something=<script>alert(’’XSS’’)</script>
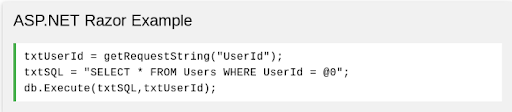
SQL INJECTION VULNERABILITY
SQL injection is a code injection technique used to attack data-driven applications, in which nefarious SQL statements are inserted into an entry field for execution. This technique can be used for various purposes, including:
- Leaking sensitive information from the database (e.g., password).
- Dumping all of the contents of the database to an attacker or another party with access to it (e.g., via web server).
Injection code example:
When “101 OR 1=1” is passed instead of just “101,” this is a very common example of SQL injection.
Authentication and Session Management weaknesses
Authentication and session management weaknesses are the most common types of security vulnerabilities.
Authentication is the process of confirming the identity of an entity, usually by presenting credentials such as passwords or keys. Session management is the process by which an application manages sessions between two or more entities to maintain some level of continuity between their interactions over time.
If you don’t have a password on your site, someone could log into it and use it as their own account! This means that if they could access data from another user’s account, they could also gain access to any information stored within that account – including personal details like addresses, bank accounts, etc…
Sensitive Data Exposure
Sensitive data can be used to identify an individual, such as a person’s name, address, social security number, credit card number, or phone number. This information is often used in applications that require access control and authorization services.
However, it’s not just banks with sensitive data on their servers – any website can also store this information! The following are some examples:
- Credit card numbers;
- Social security numbers;
- Passwords (and their corresponding hashes);
You can simply check leaked data from the surf-web by using the HIBP website; more about HIBP can be read in our previous blog post.
Using components with known vulnerabilities.
If you’re building a website, there are some components that you should never use. They might be perfectly functional in their normal state and could even be helpful to your site. However, when combined with other code or plugins, these components can cause vulnerabilities, allowing attackers to gain access to the underlying system and perform unauthorized actions.
For example: if you have an image slider plugin installed on your site (which typically depends on jQuery). Any attacker who gains access to the jQuery library can change what images appear in the slider by manipulating its source code. And this will affect all users who visit your website!
Broken Access Control: A vulnerability that allows unauthorized users to access data or perform actions within the application.
Access control is a system that determines whether a user can access a resource. It is based on the principle of least privilege, which means that only those who need access to perform their duties should have it. This helps prevent unauthorized users from accessing data or performing actions within an application.
Access controls can be implemented in many ways:
- System-level access control – This type of security control includes things such as passwords and security tokens. These systems are usually built into operating systems or middleware products like Apache Web Server or Tomcat Application Server. They’re designed to protect large amounts of information over a long period without requiring much maintenance or additional effort from administrators. For example, You could buy yourself some fancy new antivirus software that protects your computer against viruses but does nothing about hackers trying to break into them via reverse engineering techniques. Hence, I recommend using something else since this one doesn’t offer any protection against this kind of threat either.
Identifying vulnerabilities in web applications is an important skill for any security expert, so here are a few popular websites to help you boost your hacking skills.
- HackerOne is a community platform that helps hackers find jobs and employers find skilled security professionals. They have an interactive map showing all the publicly disclosed vulnerabilities in their database with details about each vulnerability, including when it was discovered, what type of software it affects, and if patches are available for those who know how to patch them (if any). You can search for specific vulnerabilities such as SQLi, XSS, or even DDoS attack techniques by entering keywords into their search bar at https://www.hackerone.com/search/.
- Fixpark is an online platform that enables website owners and ethical hackers to identify weak links on the website. Detecting vulnerabilities using publicly available data and providing a quick overview of website security as black hats see first-time visitors. Using the OWASP Top 10 vulnerabilities as a foundation and testing them all.
Conclusion
We hope you found our overview of web application security useful. You can now search the internet for more detailed guides to becoming a white hat hacker.





